Severity
High
Analysis Summary
Cybersecurity researchers have uncovered new details about a remote access trojan (RAT) known as Deuterbear, utilized by the China-linked BlackTech threat group in a cyber espionage campaign targeting the Asia-Pacific region.
Deuterbear, a more advanced variant of the previously known Waterbear malware, includes enhancements such as shellcode plugin support anti-memory scanning and HTTPS for command-and-control (C&C) communication. This malware uses a two-stage infection process to gain access to computer systems, researchers said in a new analysis.
BlackTech, active since at least 2007 and is also known as Circuit Panda, Earth Hundun, HUAPI, Manga Taurus, Palmerworm, Red Djinn, and Temp.Overboard, has long relied on Waterbear for its cyberattacks. Waterbear employs DLL side-loading through a patched legitimate executable to launch a loader that decrypts and executes a downloader which then retrieves the RAT module from a C&C server. This two-stage infection process involves using the first Waterbear RAT as a plugin downloader while the second acts as a backdoor to harvest sensitive information via 60 commands.
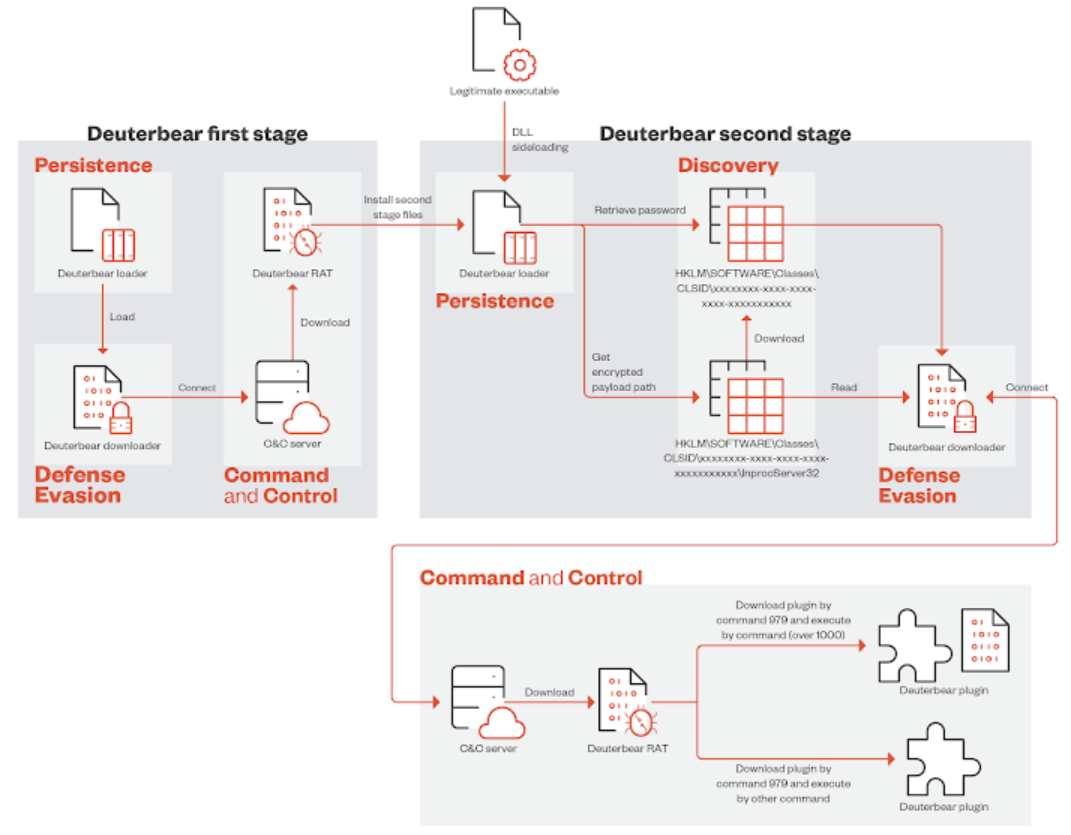
Deuterbear's infection pathway mirrors that of Waterbear but with modifications. It also uses a two-stage process, with the first stage employing a loader to fetch Deuterbear RAT which then establishes persistence through a second-stage loader via DLL side-loading. This process effectively removes all first-stage components after persistence is achieved, making the malware difficult to analyze in non-target environments. Deuterbear retains only essential commands adopting a plugin-based approach to enhance its functionality and evade detection.
In parallel, another cyber campaign has been identified targeting U.S. organizations involved in artificial intelligence (AI). This campaign employs a customized variant of Gh0st RAT known as SugarGh0st RAT to infiltrate academic, private industry, and government entities. The attacks are highly targeted involving AI-themed phishing messages that deploy the SugarGh0st payload through a JavaScript dropper. The campaign's goal appears to be the theft of sensitive information related to generative AI possibly in response to U.S. efforts to restrict China's access to advanced AI technologies.
These developments underscore the evolving nature of cyber threats from state-aligned actors like BlackTech. Both Deuterbear and SugarGh0st RAT represent sophisticated tools aimed at advancing China's strategic interests through cyber espionage. The continued evolution of these malware variants highlights the importance of robust cybersecurity measures and international cooperation to counter such threats.
Impact
- Cyber Espionage
- Remote Unauthorized Access
- Sensitive Information Theft
Indicators of Compromise
MD5
- b5337cbb312e3e4e0d1ed8ca9dd0937e
- 99a6a0b295346d42928068931d702841
SHA-256
- 974c407dd918ccba245da0fb9d5a68f123c78aacfa85cdaba2271d6ad81380ae
- 3d8512a513e5f94ce49a742ae3e4853775f05d7481b29bfacef4316d7ba3bde2
SHA1
- e1a749cde087d3b922a0ce3ab8556f4b8c63a446
- b5d7ff93ccd8b38cb6bf075fa6c03b790e9c58a3
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Be vigilant when downloading software and double-check the URL to see if it is legitimate.
- Never download software from untrusted sources.
- Download apps only from official app stores like Google Play Store or Apple App Store. Avoid downloading apps from third-party websites or unofficial sources.
- Review the permissions requested by apps before installing them. Be cautious of apps that request unnecessary permissions or access to sensitive data.
- Do not download documents attached in emails from unknown sources and strictly refrain from enabling macros when the source isn’t reliable.
- Keep your operating system and apps up-to-date with the latest security patches and updates
- Enable antivirus and anti-malware software and update signature definitions on time. Using multi-layered protection is necessary to secure vulnerable assets.
- Along with network and system hardening, code hardening should be implemented within the organization so that their websites and software are secure. Use testing tools to detect any vulnerabilities in the deployed codes.
- Maintain cyber hygiene by updating your anti-virus software and implementing a patch management lifecycle.
- Be cautious of unsolicited messages, emails, or links, especially from unknown or suspicious sources. Avoid clicking on suspicious links or downloading attachments from untrusted sources.
- Patch and upgrade any platforms and software timely and make it into a standard security policy. Prioritize patching known exploited vulnerabilities and zero-days.
- Regularly backup your data to a secure location, such as a cloud storage service or external hard drive.
- Develop and regularly update an incident response plan that outlines the steps to take in case of a security breach. Test the plan through simulations to ensure its effectiveness.

