Severity
High
Analysis Summary
Phishing PDF documents purporting to be from the Prime Minister's Office of Pakistan and the Ministry of Foreign Affairs (MOFA) have been discovered recently, as part of a sophisticated cyber campaign carried out by threat actors thought to be part of the Sidewinder APT group.
The campaign revolves around a phishing PDF file titled "Outstanding Payment of Tender upload fee PPRA.pdf," which is themed as a document from the Office of the Prime Minister of Pakistan. This PDF file evades all antivirus solutions, raising significant concerns about the potential impact on targeted systems.
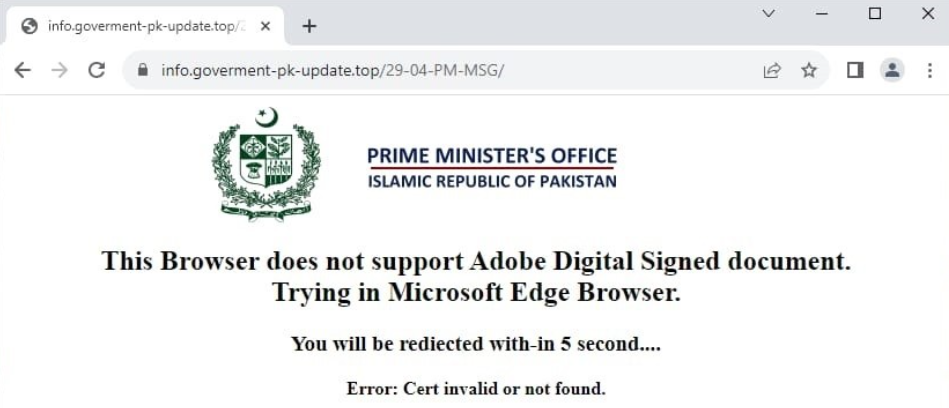
The initial access is obtained using spear-phishing link techniques by including clickable URLs in the PDF lure. The adversary may use client execution exploitation techniques to exploit client apps and run code. The attackers then disguise their malicious activities through masquerading, storing files inside user directories, and hiding artifacts, such as hidden windows.
The campaign employs several techniques for OS credential dumping, such as using web session cookies, looking for passwords that aren't secure, and getting credentials from web browsers and password databases. The threat actors obtain data about the system and installed applications through registry queries and system information discovery. The data is gathered from local computers, and the intruders especially search for sensitive and interesting files.
The attackers also interact and blend in with the current traffic by using encrypted channels and application layer protocols, and disrupting system availability and network resources is achieved by data deletion. This campaign shows how threat actors keep evolving their methods for achieving their goals of data theft and cyber espionage. Organizations need to stay vigilant when downloading attachments or clicking on links received in emails from unknown senders.
Impact
- Code Execution
- Sensitive Data Theft
- Credential Theft
- Data Loss
Indicators of Compromise
Domain Name
- info.goverment-pk-update.top
MD5
- d4eb4cee8aeb6f2ea36afadeda9dbb23
- 38f96b882363cb659d4cabec49bf605c
SHA-256
- 23f3a046884bf94ec706f98000a9efbda48455b4dd86f0665409937b1fb811cb
- 8a6e381ab6f1d2ab74e3ee232680d5991c9f751241a6a0c3f0d9082d2cf61a05
SHA1
- f3d38a0cc1f4e0a8ac734fdf035ebff93158aa05
- f879990d7d29a44f0cb14e9da4ef33ac90c0db8c
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Emails from unknown senders should always be treated with caution.
- Never trust or open links and attachments received from unknown sources/senders.
- Maintain cyber hygiene by updating your antivirus software and implementing a patch management lifecycle.
- Patch and upgrade any platforms and software on time and make it into a standard security policy. Prioritize patching known exploited vulnerabilities and zero-days.
- Enable antivirus and antimalware software and update signature definitions on time. Using multilayered protection is necessary to secure vulnerable assets.
- Enforce strong password policies across the organization. Encourage the use of complex passwords and enable multifactor authentication (MFA) wherever possible to add an extra layer of security.
- Deploy reliable endpoint protection solutions that include antivirus, antimalware, and host-based intrusion prevention systems (HIPS) to detect and block malicious activities.
- Utilize web filtering and content inspection tools to block access to malicious websites and prevent users from downloading malicious files.
- Deploy IDPS solutions to detect and block suspicious network traffic and intrusions.
- Conduct regular vulnerability assessments and penetration testing to identify weaknesses in the network infrastructure and address them before attackers exploit them.
- Continuously monitor network traffic and security logs for any signs of suspicious activities. Stay updated on the latest threat intelligence to understand the tactics, techniques, and procedures (TTPs) employed by the Sidewinder APT group and other threat actors.

