Severity
High
Analysis Summary
Over the previous five years, cybersecurity experts have found various campaigns that planted millions of malicious "imageless" containers on Docker Hub, highlighting once again how supply chain attacks could be facilitated by open-source registries.
The researchers explained in a report, “Over four million of the repositories in Docker Hub are imageless and have no content except for the repository documentation.”
Furthermore, there is no relationship between the documentation and the container. Rather, it's a website created to trick people into visiting websites that host malware or engage in phishing. 2.81 million of the 4.6 million imageless Docker Hub repositories that were found are allegedly part of three large campaigns that served as landing pages to divert gullible people to fraudulent websites.
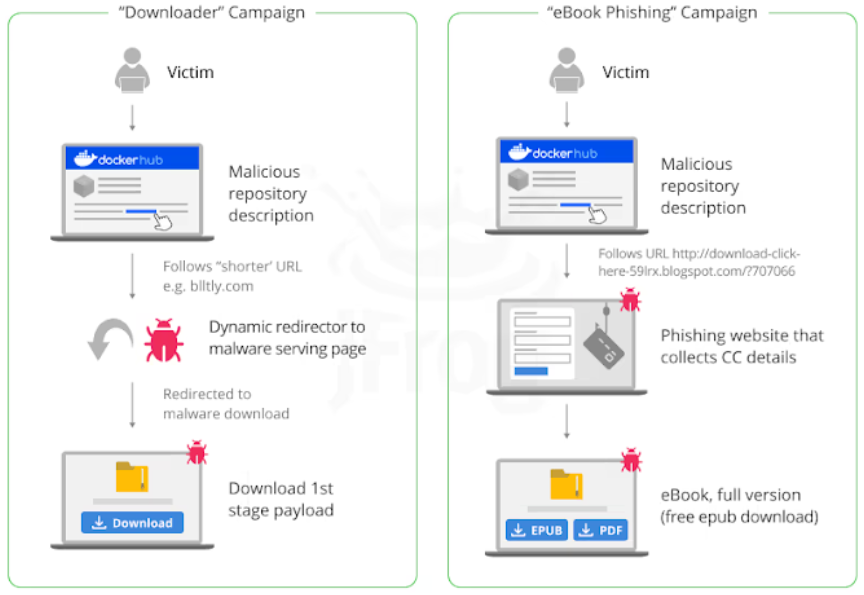
- Downloader campaign (repositories created between September 2023 and the first half of 2021) that advertises links to allegedly pirated content or video game cheats, but either point to a malicious source directly or to a legitimate source that has JavaScript code in it that, after 500 milliseconds, redirects to the malicious payload.
- E-book phishing campaign refers to repositories that were established in the middle of 2021. It takes visitors looking for e-books to a malicious website, where they are then asked to provide their credit card information to obtain the e-book.
- Website campaign (thousands of repositories produced every day between April 2021 and October 2023), which in certain circumstances has a link to the online diary-hosting service Penzu or an innocuous text indicating that it might have been utilized in the early stages of testing.
The Downloader campaign's payload is made to communicate with a command-and-control (C2) server and send system metadata; the server will then reply with a link to software that has been cracked. The attacks are thought to be a part of a bigger malware operation that may include monetization schemes like adware, which profit off the distribution of third-party software.
However, the precise purpose of the website cluster is still unknown, the campaign is also being spread on websites with slack content monitoring guidelines. The threat actors employed 208,739 fictitious identities in total, according to researchers, to build the malicious and undesired repositories. Since then, Docker has removed every one of them after being responsibly disclosed.
The fact that users are initially limited in their options for self-defense beyond being cautious is the most worrisome feature of these three campaigns. With great motivation, these threat actors are luring victims with the trustworthiness of the Docker Hub brand.
Impact
- Identity Theft
- Financial Loss
- Sensitive Data Theft
Indicators of Compromise
Domain Name
- failhostingpolp.ru
- gts794.com
- miimms.com
- vittuv.com
- soneservice.shop
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Be vigilant when downloading software and double-check the URL to see if it is legitimate.
- Never download software from untrusted sources.
- Download apps only from official app stores like Google Play Store or Apple App Store. Avoid downloading apps from third-party websites or unofficial sources.
- Review the permissions requested by apps before installing them. Be cautious of apps that request unnecessary permissions or access to sensitive data.
- Do not download documents attached in emails from unknown sources and strictly refrain from enabling macros when the source isn’t reliable.
- Keep your operating system and apps up-to-date with the latest security patches and updates
- Enable antivirus and anti-malware software and update signature definitions on time. Using multi-layered protection is necessary to secure vulnerable assets.
- Along with network and system hardening, code hardening should be implemented within the organization so that their websites and software are secure. Use testing tools to detect any vulnerabilities in the deployed codes.
- Maintain cyber hygiene by updating your anti-virus software and implementing a patch management lifecycle.
- Be cautious of unsolicited messages, emails, or links, especially from unknown or suspicious sources. Avoid clicking on suspicious links or downloading attachments from untrusted sources.
- Patch and upgrade any platforms and software timely and make it into a standard security policy. Prioritize patching known exploited vulnerabilities and zero-days.
- Regularly backup your data to a secure location, such as a cloud storage service or external hard drive.
- Develop and regularly update an incident response plan that outlines the steps to take in case of a security breach. Test the plan through simulations to ensure its effectiveness.

