Severity
High
Analysis Summary
The recently discovered zero-day vulnerability in Palo Alto Networks PAN-OS software has been exploited by threat actors since March 26, 2024, more than three weeks before its discovery.
The company said, “Palo Alto Networks is aware of malicious exploitation of this issue. We are tracking the initial exploitation of this vulnerability under the name Operation MidnightEclipse, as we assess with high confidence that known exploitation we’ve analyzed thus far is limited to a single threat actor.”
The security vulnerability, identified as CVE-2024-3400 (CVSS score: 10.0), is a command injection flaw that allows unauthorized attackers to run any code on the firewall with root privileges. It is important to note that this problem only affects firewall installations running PAN-OS 10.2, PAN-OS 11.0, and PAN-OS 11.1 with GlobalProtect gateway and device telemetry enabled.
Using the vulnerability, Operation MidnightEclipse comprises setting up a cron job that runs once every minute to retrieve commands that are hosted on an external server. The commands are then run using the bash shell. It is claimed that the attackers manually maintained the command-and-control (C2) server's access control list (ACL) to make sure that only the device connecting to it could access it.
Although the researchers, who discovered an in-the-wild exploitation of CVE-2024-3400 on April 10, 2024, are tracking as UPSTYLE, the precise nature of the command is unknown, but it is suspected that the URL acts as a delivery vehicle for a Python-based backdoor on the firewall. The URL is hosted on a different server. The purpose of the Python script is to write and run a second Python script ("system.pth"), which then decodes and activates the embedded backdoor component that sends commands to the threat actor's file named "sslvpn_ngx_error.log." The output of the process is saved in a different file called "bootstrap.min.css." The fact that the files used to write the results and extract the commands are both authentic files connected to the firewall is what makes the attack chain the most intriguing.
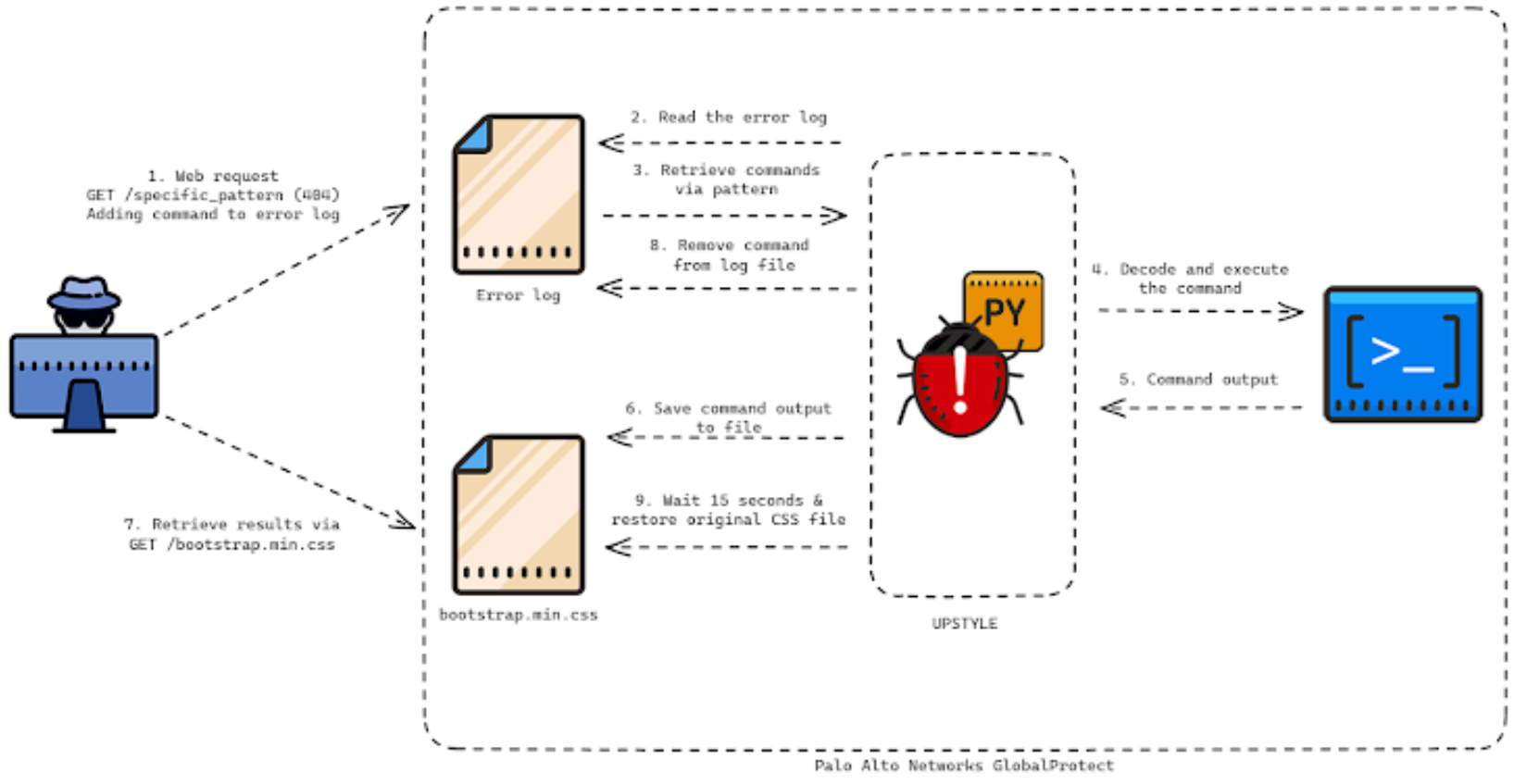
The threat actor forges specifically crafted network requests to a fictitious web page that contains a particular pattern, which is how the commands are recorded to the web server error log. Then, to decode and execute the command within, the backdoor parses the log file and looks for the line that matches the same regular expression. After that, the script will start a new thread and use it to execute the restore function. After a 15-second sleep, the restore function writes the original contents of the bootstrap.min.css file back into it and restores the access and modified times to their initial values.
Since the results must be exfiltrated within 15 seconds of the file being overwritten, it seems that the primary objective is to prevent leaving any evidence of the command outputs. According to researchers, the threat actor was seen remotely taking advantage of the firewall to download more tools, build a reverse shell, move into internal networks, and eventually steal data. Right now, it's uncertain how big the campaign will be.
The attacker's skill and speed point to a highly competent threat actor with a defined playbook of what to access to achieve their goals. It is advised that organizations monitor any internal lateral movement from their Palo Alto Networks GlobalProtect firewall device. To lessen possible dangers, federal entities must implement the fixes by April 19 according to the U.S. Cybersecurity and Infrastructure Security Agency (CISA), which also added the vulnerability to its list of known exploited vulnerabilities (KEV) as a result of the development. Palo Alto Networks is anticipated to make the vulnerability's remedies available by April 14.
Impact
- Code Execution
- Unauthorized Access
- Sensitive Information Theft
Indicators of Compromise
MD5
- 0c1554888ce9ed0da1583dbdf7b31651
SHA-256
- 3de2a4392b8715bad070b2ae12243f166ead37830f7c6d24e778985927f9caac
SHA-1
- 988fc0d23e6e30c2c46ccec9bbff50b7453b8ba9
URL
- http://172.233.228.93/policy
- http://172.233.228.93/patch
Remediation
- Refer to Palo Alto Security Advisory for patch, upgrade, or suggested workaround information.
- Block all threat indicators at your respective controls.
- Search for Indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Implement multi-factor authentication to add an extra layer of security to login processes.
- Regularly monitor network activity for any unusual behavior, as this may indicate that a cyberattack is underway.
- Organizations need to stay vigilant and follow best practices for cybersecurity to protect their systems and data from potential threats. This includes regularly updating software and implementing strong access controls and monitoring tools.
- Develop a comprehensive incident response plan to respond effectively in case of a security breach or data leakage.
- Maintain regular backups of critical data and systems to ensure data recovery in case of a security incident.
- Adhere to security best practices, including the principle of least privilege, and ensure that users and applications have only the necessary permissions.
- Establish a robust patch management process to ensure that security patches are evaluated, tested, and applied promptly.
- Conduct security audits and assessments to evaluate the overall security posture of your systems and networks.
- Implement network segmentation to contain and isolate potential threats to limit their impact on critical systems.


