Severity
High
Analysis Summary
The Editbot stealer, a newly discovered Python-based information stealer on the dark web, poses a significant threat to social media users’ sensitive data, as revealed by security researchers. Initially found in a WinRAR archive file on VirusTotal with low detection rates, the Editbot stealer employs a meticulously designed multi-stage attack to avoid detection, download additional payloads, and establish persistence on victims’ systems.
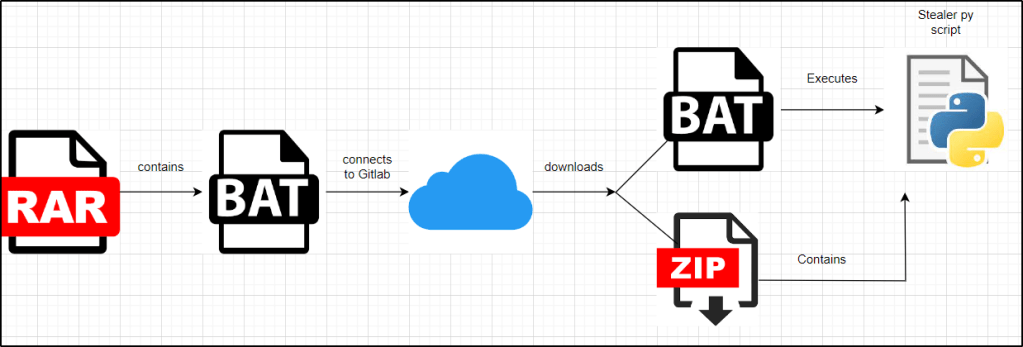
Threat actors behind this campaign utilize open-source code-sharing platforms like Gitlab to fetch subsequent stage payloads. The Python-based stealer, capable of extracting critical information such as passwords and cookies, transmits the stolen data to the attackers via a Telegram channel.
An investigation on December 5th identified a potentially malicious RAR file on VirusTotal, linked to a social media scam exploiting the allure of popular products to deceive users. The Editbot stealer employs a multi-stage infection strategy involving a malicious batch file and a JSON file, ensuring persistence through PowerShell commands that download and execute the Python-based stealer at each login session.
Technical analysis reveals the Editbot stealer’s sophistication, with a Python script enumerating processes, extracting sensitive data from various browsers, and sending it to a Telegram channel. The stealer captures information from Chrome, Firefox, Edge, Opera, Brave-Browser, CocCoc, and Chromium, saving files like Cookies and Login Data in the %temp% folder. It decrypts passwords, stores login details in “pass.txt,” and extracts cookie information into “cookie.txt” if associated with a social media site. This comprehensive data exfiltration underscores the severity of the Editbot stealer’s impact on user privacy and security.
Impact
- Sensitive Information Theft
- Credential Theft
- Data Exfiltration
Indicators of Compromise
MD5
- ca5bee4607ddd920729e5c2b4fc89bbc
- e9e4cd111cadcf94c469365354df3fdc
- 669e7ac187fb57c4d90b07d9a6bb1d42
- f23465088d26e90514b5661936016c05
- c3a447c5c6c73d80490347c1b4afe9d5
SHA-256
- fd8391a1a0115880e8c3ee2e76fbce741f1b3c5fbcb728b9fac37c21e9f6d7b7
- d13aba752f86757de6628e833f4fdf4c625f480056e93b919172e9c309448b80
- 3f7bd47fbbf1fb0a63ba955c8f9139d6500b6737e5baf5fdb783f0cedae94d6d
- 9d048e99bed4ced4f37d91a29763257a1592adb2bc8e17a66fa07a922a0537d0
- bc3993769a5f82e454acef92dc2362c43bf7d6b6b203db7db8803faa996229aa
SHA-1
- feff390b99dfe7619a20748582279bc13c04f52a
- 18e96d94089086848a0569a1e1d8051da0f6f444
- eed59a282588778ffbc772085b03d229a5d99e35
- 93d70f02b2ee2c4c2cd8262011ed21317c7d92de
- cf019e96e16fdaa504b29075aded36be27691956
Remediation
- Block all threat indicators at your respective controls.
- Search for Indicators of compromise (IOCs) in your environment utilizing your respective security controls
- Passwords – Ensure that general security policies are employed including implementing strong passwords, correct configurations, and proper administration security policies.
- Admin Access – limit access to administrative accounts and portals to only relevant personnel and make sure they are not publicly accessible.
- Patch and upgrade any platforms and software timely and make it into a standard security policy. Prioritize patching known exploited vulnerabilities and zero-days.
- Emails from unknown senders should always be treated with caution.
- Never trust or open links and attachments received from unknown sources/senders.
- Enable antivirus and anti-malware software and update signature definitions on time. Using multi-layered protection is necessary to secure vulnerable assets
- Along with network and system hardening, code hardening should be implemented within the organization so that their websites and software are secure. Use testing tools to detect any vulnerabilities in the deployed codes.
- Maintain up-to-date patches and antivirus software to prevent the exploitation of known vulnerabilities.
- Organizations should conduct regular vulnerability assessments and penetration testing to identify and mitigate potential security weaknesses.
- Implement robust security measures such as two-factor authentication, endpoint detection and response (EDR) tools, and employee security awareness training.

