Severity
High
Analysis Summary
According to recent reports, suspected Russian threat actors have been targeting users in the crypto industry in Eastern Europe with fake job opportunities. The attackers are using these job offers as a lure to trick users into downloading and installing malware onto their systems, which is designed to steal sensitive information such as login credentials and cryptocurrency wallet keys.
Recent reports suggest that alleged Russian threat actors have been using multiple highly obfuscated and under-development custom loaders to deliver the Enigma info-stealing malware. Enigma is a type of malware that is designed to steal sensitive information, including cryptocurrency wallet data, login credentials, and personal information. The use of custom loaders by the attackers makes it more difficult for traditional antivirus and cybersecurity measures to detect and block the malware.
The attackers are also exploiting a known vulnerability in an Intel driver (CVE-2015-2291) to conduct BYOVD (Bring Your Own Vulnerable Device) attacks, which allows them to reduce the token integrity of Microsoft Defender and bypass security measures.
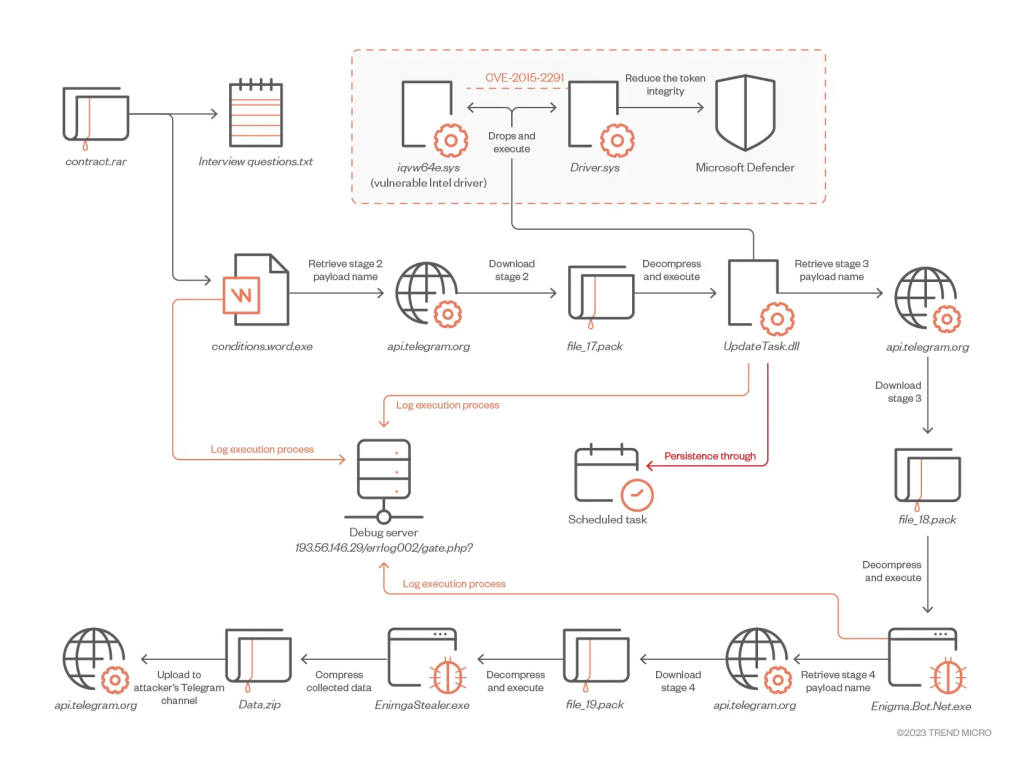
The attackers are said to be using a rogue RAR archive file that is distributed via phishing or social media platforms. The archive file contains two documents, one of which is a .TXT file that includes a set of sample interview questions related to cryptocurrency.
When the victim opens the .TXT file, it contains a hyperlink that redirects them to a malicious website that downloads the Enigma info-stealing malware.
“To download the next stage payload, the malware first sends a request to the attacker-controlled Telegram channel https://api[.]telegram[.]org/bot{token}/getFile to obtain the file_path. This approach allows the attacker to continuously update and eliminates reliance on fixed file names.”
UpdatTask.dll, the second-stage malware, is a C++ dynamic-link library (DLL) with two export functions, DllEntryPoint, and Entry. This payload disables Microsoft Defender by exploiting the CVE-2015-2291 flaw using the BYOVD approach. The malware next downloads and runs the third-stage payload, which downloads the Enigma Stealer.
The Enigma stealer is a type of malware that is capable of harvesting sensitive information, recording keystrokes, and capturing screenshots. The stolen data is then exfiltrated through the messaging app Telegram. The malware is designed to target various web browsers and applications, including Google Chrome, Microsoft Edge, Microsoft Outlook, Telegram, Signal, OpenVPN, and others. The Enigma stealer can be used to steal a wide range of sensitive information, including login credentials, financial information, and personal data.
Similar to recent campaigns, the Fake employment offers method is also used by the North Korean-backed Lazarus Group in its crypto-attacks. Russian threat actors’ use of this tactic demonstrates a continuous and lucrative attack vector.
“Furthermore, this case highlights the evolving nature of modular malware that employ highly obfuscated and evasive techniques along with the utilization of continuous integration and continuous delivery (CI/CD) principles for continuous malware development.” they conclude.
To protect themselves against the recent Enigma malware campaign, organizations should remain vigilant against phishing attacks and educate their employees about the risks of clicking on suspicious links or opening unsolicited email attachments. Individuals should also be cautious of social media posts or phishing attempts that offer job opportunities, especially during times of economic uncertainty.
Impact
- Sensitive Information Theft
- Screenshots Capturing
- Record Keystrokes
Indicators of Compromise
MD5
- 955415fe5d42f148e7dce6c84d2d4e2a
- db6a2e22498c3ee54d663f11ccbfff86
- 1898ceda3247213c084f43637ef163b3
- 50949ad2b39796411a4c7a88df0696c8
SHA-256
- a25b7eb9e51c623cbce4defa573d9b8f45c948c1c6ab48a22c344fe003fbdd4c
- d4d36f5aae7fdb6b88b5aae888947d7e6e3bfaab67b584ee71bd316cedc80f00
- 4429f32db1cc70567919d7d47b844a91cf1329a6cd116f582305f3b7b60cd60b
- 8dc192914e55cf9f90841098ab0349dbe31825996de99237f35a1aab6d7905bb
SHA-1
- 5955e81b3eb12cfe63eb3595f34b09db826eb9b2
- c1fc64004afb19e6750a9866286175519feb52c6
- d04e5db5b6c848a29732bfd52029001f23c3da75
- 67a502395fc4193721c2cfc39e31be11e124e02c
Remediation
- Block all threat indicators at your respective controls.
- Search for Indicators of compromise (IOCs) in your environment utilizing your respective security controls
- Emails from unknown senders should always be treated with caution.
- Never trust or open ” links and attachments received from unknown sources/senders.
- Organizations should remain vigilant against phishing attacks and educate their employees about the risks of clicking on suspicious links or opening unsolicited email attachments.
- Individuals should also be cautious of social media posts or phishing attempts that offer job opportunities, especially during times of economic uncertainty.
- Implement a multilayered defense strategy that includes comprehensive security solutions such as XDR. XDR can detect, scan, and block malicious URLs across the modern threat landscape.
- Maintain cyber hygiene by updating your anti-virus software and implementing a patch management lifecycle.
- Patch and upgrade any platforms and software timely and make it into a standard security policy. Prioritize patching known exploited vulnerabilities and zero-days.

