Severity
High
Analysis Summary
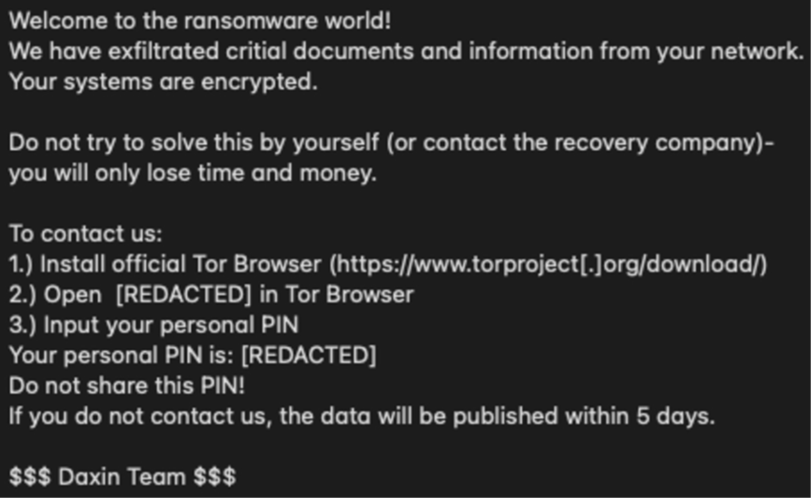
The Daixin Team cybercrime gang is actively pursuing ransomware operations against U.S. companies, mostly in the Healthcare and Public Health (HPH) Sector, according to CISA, the FBI, and the Department of Health and Human Services (HHS).
A ransomware and data extortion group, The Daixin Team, has been operational since at least June 2022. The group concentrated its ransomware activities on the HPH Sector with the goal of distributing ransomware, exfiltrating patient health information (PHI), and threatening to reveal the stolen data if a ransom is not paid.
In a joint advisory released, the government agencies also provided indications of compromise (IOCs) and tactics, methods, and procedures (TTPs) to aid security experts in identifying and thwarting attacks utilising this ransomware strain.
“Daixin actors gain initial access to victims through virtual private network (VPN) servers. In one confirmed compromise, the actors likely exploited an unpatched vulnerability in the organization’s VPN server [T1190]. In another confirmed compromise, the actors used previously compromised credentials to access a legacy VPN server [T1078] that did not have multifactor authentication (MFA) enabled. The actors are believed to have acquired the VPN credentials through the use of a phishing email with a malicious attachment [T1598.002].”
Daixin actors use Secure Shell (SSH) and Remote Desktop Protocol (RDP) to move laterally after acquiring access to the target’s VPN server.
To distribute the ransomware, the attackers utilize a variety of techniques, including credential dumping and passing the hash.
This privileged access is also used to “get access to VMware vCenter Server and reset account credentials for ESXi servers in the environment,” with the same purpose of encrypting the systems with ransomware.
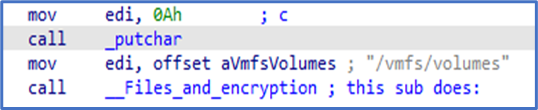
According to third-party reporting, the ransomware used by the group is based on the Babuk Locker source code.
” This third-party reporting as well as FBI analysis show that the ransomware targets ESXi servers and encrypts files located in /vmfs/volumes/ with the following extensions: .vmdk, .vmem, .vswp, .vmsd, .vmx, and .vmsn. A ransom note is also written to /vmfs/volumes/.”
Daixin Team also used Rclone and Ngrok tools to steal data from victim systems.
The following actions must be taken by health organizations to protect themselves from attacks by the Daixin Team:
- Install operating system, software, and firmware upgrades as soon as they are available. Patching VPN servers, remote access software, virtual machine software, and known exploited vulnerabilities should be prioritised.
- Consider phishing-resistant MFA mandatory for as many services as possible, especially webmail, VPNs, accounts that access critical systems, and privileged accounts that control backups.
- If you use Remote Desktop Protocol (RDP), secure and monitor it.
- Users should be taught to identify and report phishing attempts.
Furthermore, the FBI, CISA, and HHS encourage all organizations, including those in the HPH Sector, to implement the mentioned recommendations to prepare for, mitigate/prevent, and respond to ransomware occurrences.
Impact
- Patient Health Information Theft
- Credential Dumping
- Sensitive Information Theft
- File Encryption
Remediation
- Install operating system, software, and firmware upgrades as soon as they are available. Patching VPN servers, remote access software, virtual machine software, and known exploited vulnerabilities should be prioritised.
- Consider phishing-resistant MFA mandatory for as many services as possible, especially webmail, VPNs, accounts that access critical systems, and privileged accounts that control backups.
- If you use Remote Desktop Protocol (RDP), secure and monitor it.
- Users should be taught to identify and report phishing attempts.
- Use standard user accounts on internal systems instead of?administrative?accounts, which allow for overarching administrative system privileges and do not ensure least privilege.
- For more mitigations and remediations, please refer to the advisory

